Phishing Definition
Phishing is a common type of cyber attack that targets individuals through email, text messages, phone calls, and other forms of communication. A phishing attack aims to trick the recipient into falling for the attacker’s desired action, such as revealing financial information, system login credentials, or other sensitive information.
As a popular form of social engineering, phishing involves psychological manipulation and deception whereby threat actors masquerade as reputable entities to mislead users into performing specific actions. These actions often involve clicking links to fake websites, downloading and installing malicious files, and divulging private information, like bank account numbers or credit card information.
Since the mid-1990s, the term “phishing” has been used to identify hackers who use fraudulent emails to “fish for” information from unsuspecting users. However, phishing attacks have become increasingly sophisticated and are now broken down into different types, including email phishing, spear phishing, smishing, vishing, and whaling. Each type is characterized by specific channels and methods of execution – email, text, voice, social media, etc. – all with a similar underlying intention.
Previous65%of organizations reported at least one incident of data loss in 202230 millionmalicious messages sent in 2022 involved Microsoft brandingPhishing attacks reported in 2020241,324an estimated 110% increase from 2019’s reported 114,702 incidents84%of U.S. survey respondents have fallen victim to phishing96%of phishing attacks are delivered using email$14.8 millionis the average cost to an organization after becoming a victim of a phishing campaign, more than triple the amount in 2015, $3.8 millionEmployee productivity losses have increased from $1.8m in 2015 to$3.2 millionin 2021Total cost of business email compromise$2.7 billionfor 202276%increase in direct financial loss from successful phishing in 202265%of organizations reported at least one incident of data loss in 202230 millionmalicious messages sent in 2022 involved Microsoft brandingPhishing attacks reported in 2020241,324an estimated 110% increase from 2019’s reported 114,702 incidents84%of U.S. survey respondents have fallen victim to phishingNext
How Phishing Works
Whether a phishing campaign is hyper-targeted or sent to as many victims as possible, it starts with a malicious message. An attack is disguised as a message from a legitimate company. The more aspects of the message that mimic the real company, the more likely an attacker will be successful.
While attackers’ goals vary, the general aim is to steal personal information or credentials. An attack is facilitated by emphasizing a sense of urgency in the message, which could threaten account suspension, money loss, or loss of the targeted user’s job. Users tricked into an attacker’s demands don’t take the time to stop and think if the demands seem reasonable or if the source is legitimate.
Phishing continually evolves to bypass security filters and human detection, so organizations must continually train staff to recognize the latest phishing strategies. It only takes one person to fall for phishing to incite a severe data breach. That’s why it’s one of the most critical threats to mitigate and the most difficult as it requires human defenses.
Why Is Phishing a Problem?
Phishing is a significant problem because it is easy, cheap, and effective for cybercriminals to use. Phishing tactics, particularly email, require minimal cost and effort, making them widespread cyber-attacks. Victims of phishing scams may end up with malware infections (including ransomware), identity theft, and data loss.
The data that cybercriminals go after include personal identifiable information (PII)—like financial account data, credit card numbers, and tax and medical records—as well as sensitive business data, such as customer names and contact information, proprietary product secrets, and confidential communications.
Cybercriminals also use phishing attacks to gain direct access to email, social media and other accounts or to obtain permissions to modify and compromise connected systems, like point-of-sale terminals and order processing systems. Many of the biggest data breaches start with an innocent phishing email where cybercriminals gain a small foothold to build upon.
Phishing Examples
Attackers prey on fear and a sense of urgency, often using strategies that tell users their account has been restricted or will be suspended if they don’t respond to the email.
Because phishing attacks are typically sent to as many people as possible, the messaging is usually thin and generic. The following illustrates a common phishing email example.

In the above message, the user’s name is not mentioned, and the sense of urgency injects fear to trick users into opening the attachment.
The attachment could be a web page, a shell script (e.g., PowerShell), or a Microsoft Office document with a malicious macro. The macro and scripts can be used to download malware or trick users into divulging their account credentials.
In some email phishing tactics, attackers register domains that look similar to their official counterparts or they occasionally use generic email providers such as Gmail. When users receive emails, the messages might use the official company logo, but the sender’s address would not include the official company domain.How an attacker carries out a phishing campaign depends on their goals. In B2B for example, attackers may use fake invoices to trick the accounts payable department into sending money. In this attack, the sender is not important, as m. Many vendors use personal email accounts to do business.

The button in this example opens a web page with a fraudulent Google authentication form. The page attempts to scam targeted victims into entering their Google credentials so that attackers can steal accounts.
Phishing Techniques
Cybercriminals use three primary phishing techniques to steal information: malicious web links, malicious attachments and fraudulent data-entry forms.
Malicious Web Links
Phishing links take users to impostor websites or sites infected with malicious software, also known as malware. Malicious links can be disguised as trusted links and are embedded in logos and other images in an email.
Here is an example of an email received by users at Cornell University, displaying “Help Desk” as the sender’s name. However, the email did not originate from the university’s help desk but rather from the @connect.ust.hk domain. The link embedded in the email points to a page that looks like the Office 365 login page attempting to steal user credentials.

Malicious Attachments
While these may look like legitimate file attachments, they are actually infected with malware that can compromise computers and their files.

Here’s an example of a phishing email shared by international shipper FedEx on its website. This email encouraged recipients to print out a copy of an attached postal receipt and take it to a FedEx location to get a parcel that could not be delivered. Unfortunately, the attachment contained a virus that infected the recipients’ computers. Variations of these shipping scams are particularly common during the holiday shopping season.
Fraudulent Data Entry Forms
These techniques use fake forms that prompt users to fill in sensitive information—such as user IDs, passwords, credit card data, and phone numbers. Once users submit that information, it can be used by cybercriminals for various fraudulent activities, including identity theft.
Here’s an example of a fake landing page mimicking the gov.uk website. After clicking a link in a phishing email, users are routed to this fraudulent page that appears to be part of the HMRC tax collection agency. Users are told they are eligible for a refund but must complete the form.


THE PONEMON 2021 COST OF PHISHING STUDY
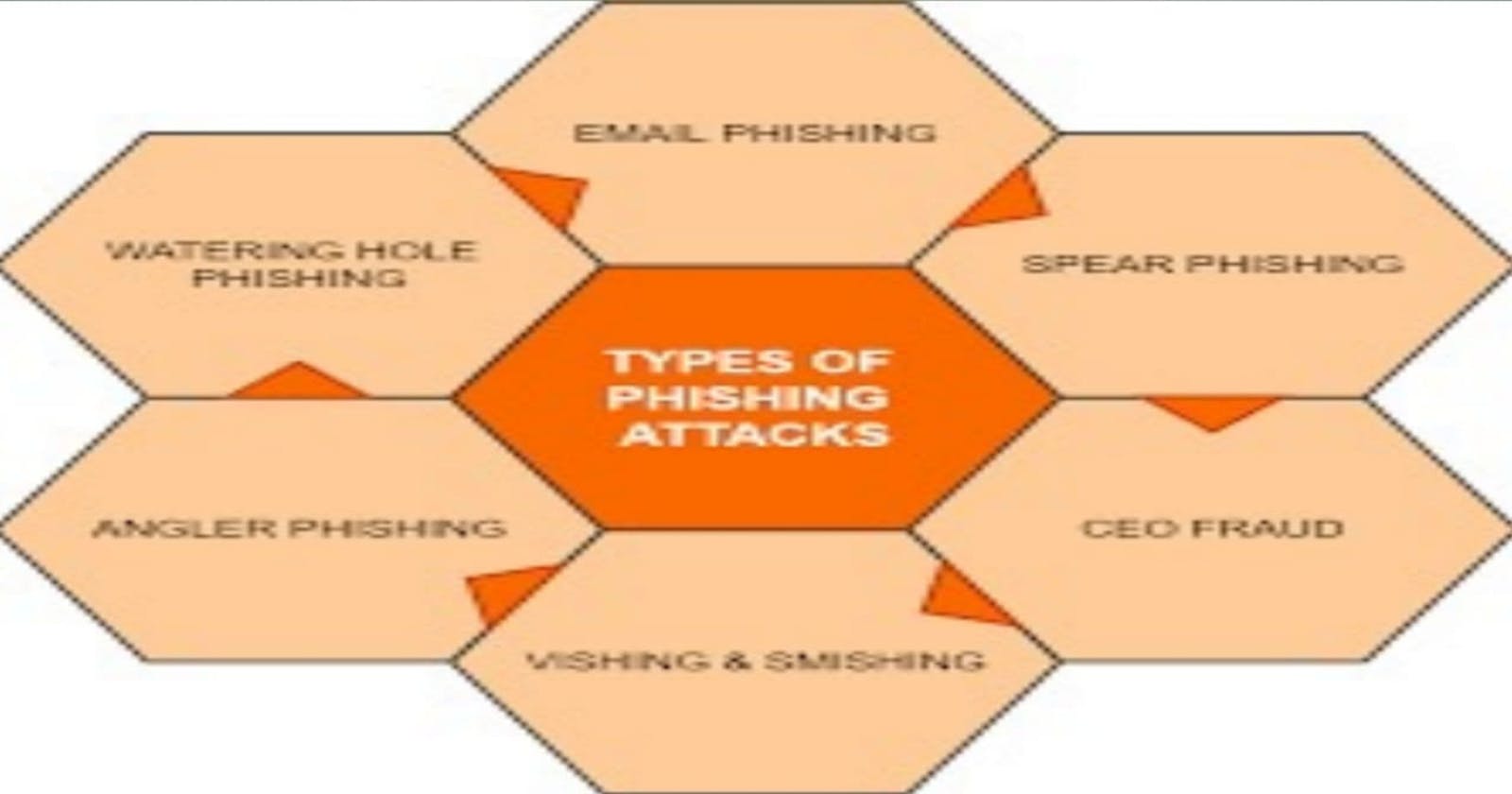
Types of Phishing Attacks
Phishing has evolved into more than simple credential and data theft. How an attacker lays out a campaign depends on the type of phishing. Types of phishing include:
Email phishing: the general term given to any malicious email message meant to trick users into divulging private information. Attackers generally aim to steal account credentials, personally identifiable information (PII) and corporate trade secrets. However, attackers targeting a specific business might have other motives.
Spear phishing: these email messages are sent to specific people within an organization, usually high-privilege account holders, to trick them into divulging sensitive data, sending the attacker money or downloading malware.
Link manipulation: messages contain a link to a malicious site that looks like the official business but takes recipients to an attacker-controlled server where they are persuaded to authenticate into a spoofed login page that sends credentials to an attacker.
Whaling (CEO fraud): these messages are typically sent to high-profile employees of a company to trick them into believing the CEO or other executive has requested to transfer money. CEO fraud falls under the umbrella of phishing, but instead of an attacker spoofing a popular website, they spoof the CEO of the targeted corporation.
Content injection: an attacker who can inject malicious content into an official site will trick users into accessing the site to show them a malicious popup or redirect them to a phishing website.
Malware: users tricked into clicking a link or opening an attachment might download malware onto their devices. Ransomware, rootkits or keyloggers are common malware attachments that steal data and extort payments from targeted victims.
Smishing: using SMS messages, attackers trick users into accessing malicious sites from their smartphones. Attackers send a text message to a targeted victim with a malicious link that promises discounts, rewards or free prizes.
Vishing: attackers use voice-changing software to leave a message telling targeted victims that they must call a number where they can be scammed. Voice changers are also used when speaking with targeted victims to disguise an attacker’s accent or gender so that they can pretend to be a fraudulent person.
“Evil Twin” Wi-Fi: spoofing free Wi-Fi, attackers trick users into connecting to a malicious hotspot to perform man-in-the-middle exploits.
Pharming: pharming is a two-phase attack used to steal account credentials. The first phase installs malware on a targeted victim and redirects them to a browser and a spoofed website where they are tricked into divulging credentials. DNS poisoning is also used to redirect users to spoofed domains.
Angler phishing: using social media, attackers reply to posts pretending to be an official organization and trick users into divulging account credentials and personal information.
Watering hole: a compromised site provides endless opportunities, so an attacker identifies a site used by numerous targeted users, exploits a vulnerability on the site, and uses it to trick users into downloading malware. With malware installed on targeted user machines, an attacker can redirect users to spoofed websites or deliver a payload to the local network to steal data.